Overview
This guide outlines how to limit local administrators on Intune managed devices. This is a great way to improve security and reduce the risk of privilege escalation attacks. This guide will remove all local administrators except for Global Administrators and Azure AD Joined Device Local Administrators.
Limiting Local Administrators
Prerequisites
- Microsoft Graph PowerShell SDK
- Intune Administrator role or higher
Step 1: Connect to MS Graph and get the Object IDs for the Directory Roles
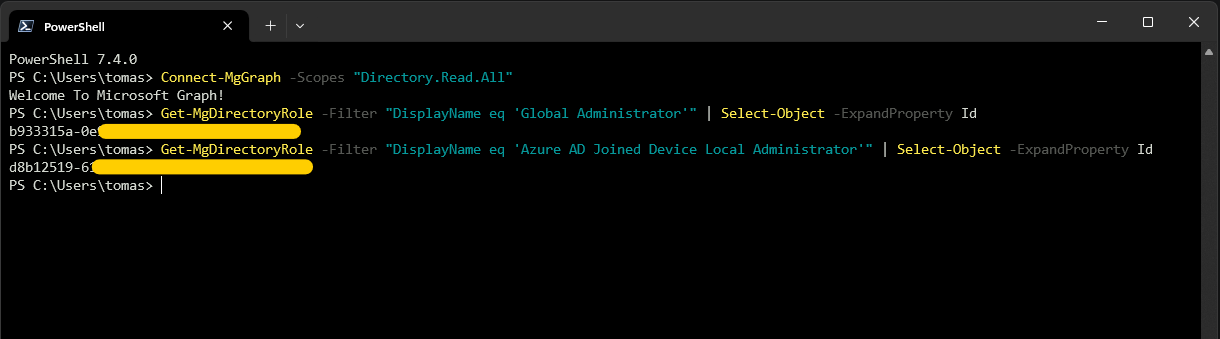
First, we need to connect to MS Graph and get the Object IDs for the Directory Roles we want to keep as local administrators. In this example, we’ll keep Global Administrators and Azure AD Joined Device Local Administrators. Take note of the Object IDs as we’ll need them later.
| |
Step 2: Convert the Object IDs to SIDs
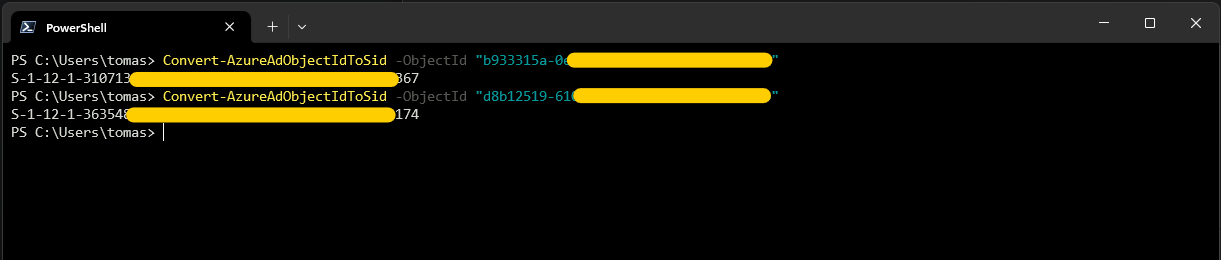
Next, we need to convert the Object IDs to SIDs. Take note of the SIDs as we’ll need them later. Run the following script and replace <Object ID> with the Object ID from the previous step, one for each role.
| |
Step 3: Create a Device Manager Policy
Now that we have the SIDs, we can create a Device Manager policy to limit local administrators.
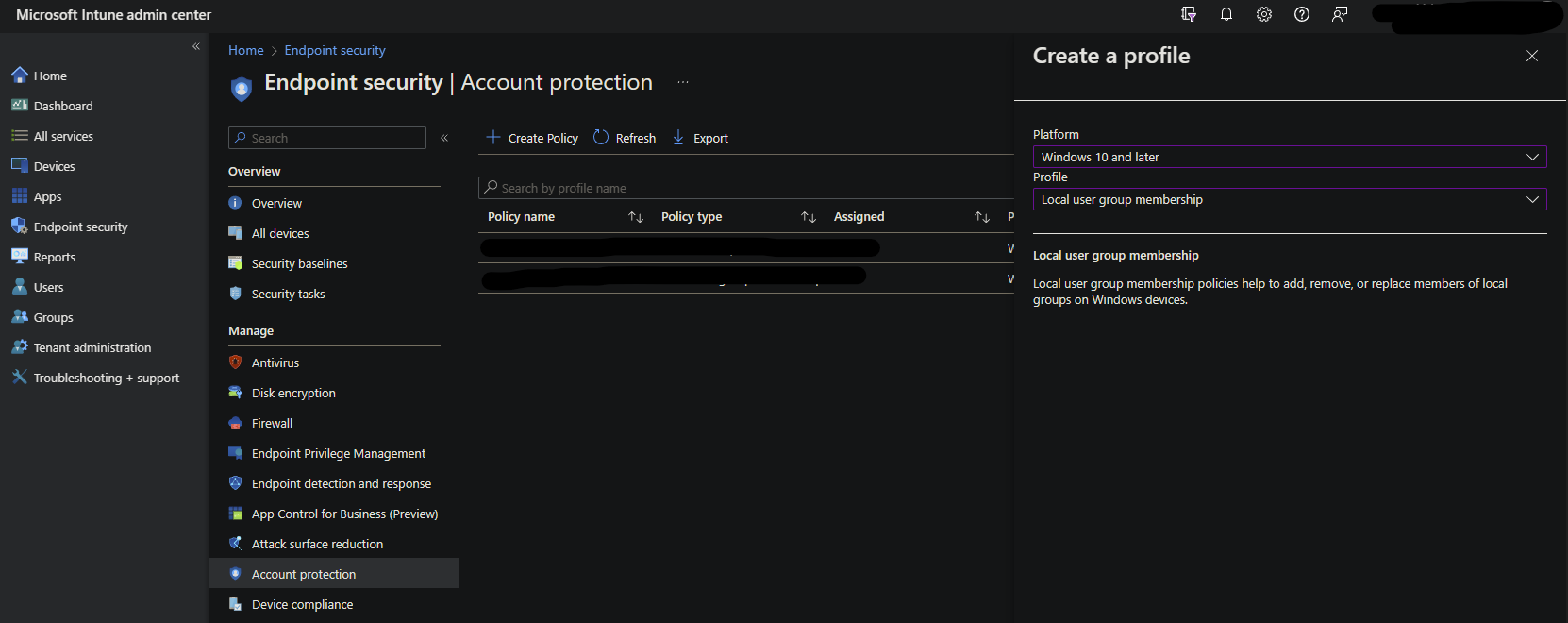
- In the Intune portal , navigate to Endpoint Security > Account Protection.
- Create a new policy for Local user group membership.
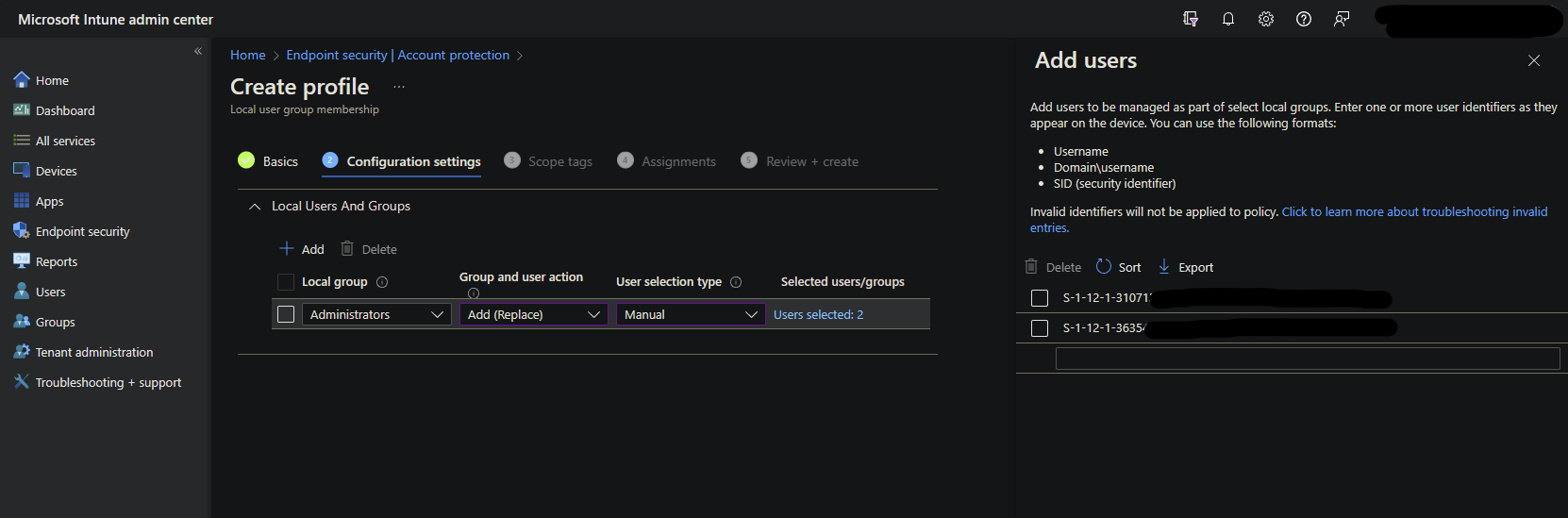
- Select the group Administrators, set the Action to Add (Replace), User selection type to Manual, and add the SIDs from the previous step.
- Set assignment to the desired groups or all devices, and save the policy.
Conclusion
This is a great way to improve security and reduce the risk of privilege escalation attacks. Some estimates say that having users run with Standard Privileges can help mitigate 94% or more of Microsoft vulnerabilities.